The Rising Cost of Data Breach
October 28, 2015IBM and the Poneman Institute released a global study in January that said the average total cost of a data breach has increased 23 percent in the last two years, up to $3.79 million.
The same study showed that the average cost paid by organizations for each lost or stolen record containing confidential information rose from $145 in 2014 to $154 in 2015. The largest increase was seen in the retail industry, where the average cost increased from $105 in 2013 to $165 in 2014.
The Cost of a Data Breach is Increasing
As today’s world becomes more and more digital, with so much sensitive data stored on drives of all sorts, optical media, cell phones, and various other forms of office equipment, there’s every reason to believe that the cost of a data breach is only going to rise over the next several years.
It’s important to know that just because a piece of technology no longer works, doesn’t mean that the information on it is no longer accessible. In fact, without destruction, most of it is pretty easily retrieved by someone who knows what they’re doing.
In 2003 researchers at MIT were able to recover 92.4 percent of sensitive information from 158 used hard drives. That sensitive information included not only corporate information, but names and contact information, emails, credit card numbers, social security numbers and medical records.
Security measures have improved dramatically since MIT’s study, and organizations have embraced the value of hiring Technology Asset Disposal Companies. While security has improved, so have hackers and data thieves. If you think that black markets where stolen information is sold only exist on TV shows and in the movies, you’ve got your head in the sand.
The following numbers should scare you a little bit: 80 percent of corporate desktops and laptops contain sensitive data. When it comes to IT personnel, only 34 percent have a secure process for hard drive destruction.
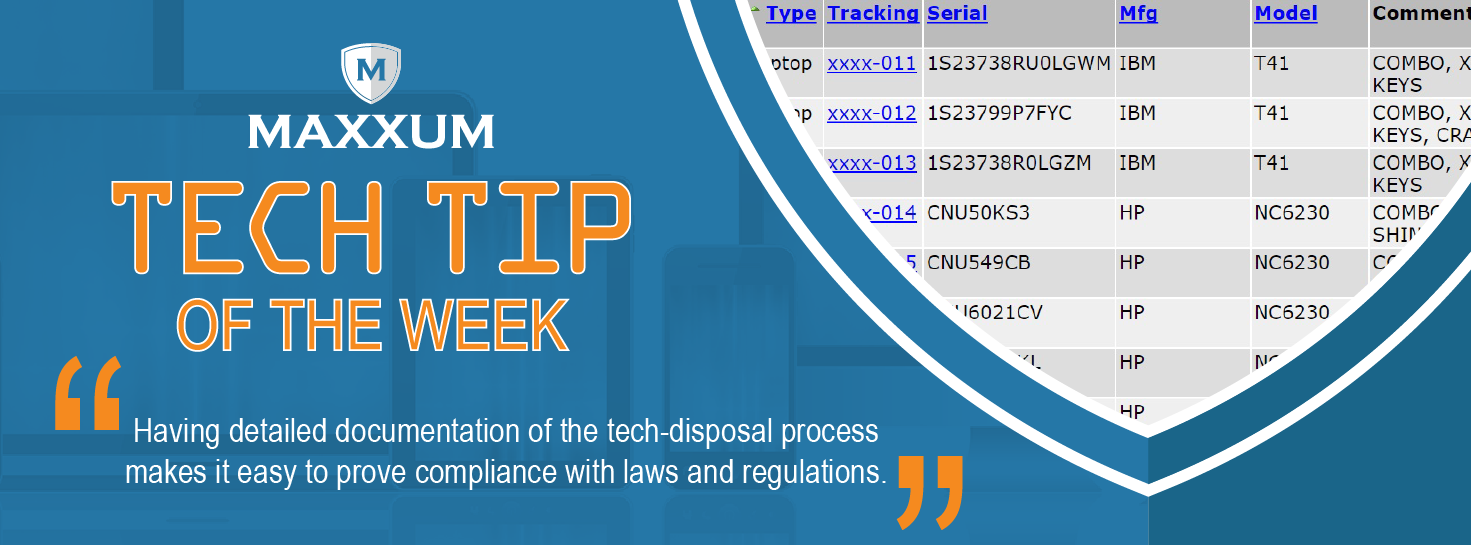
There’s far too much on the line, both monetarily and legally, for organizations not to hire experts to dispose of their technology assets when the time comes to refresh or upgrade. Avoid the rising costs of any kind of information breach by hiring an expert and trustworthy data destruction organization.