How Maxxum Helps Educational Institutions
May 5, 2017
How Maxxum Helps Educational Institutions
With the 2016-17 school year winding down, many schools are now considering IT equipment refreshes for next year and beyond. As part of their planning effort, schools will be assessing the remarketing or residual value of their current equipment to determine the viability of leasing or purchasing new equipment.
As trusted advisors to schools, colleges, universities and corporations, Maxxum helps these institutions assess the value and best disposition path for their IT assets. Maxxum’s remarketing programs are an effective way to mitigate data security risk, liquidate equipment, and actually gain a return before equipment becomes a liability due to obsolescence, disposal or recycling costs. We purchase all leading brands and types of IT equipment including tablets, laptops, desktops, networking gear, etc.
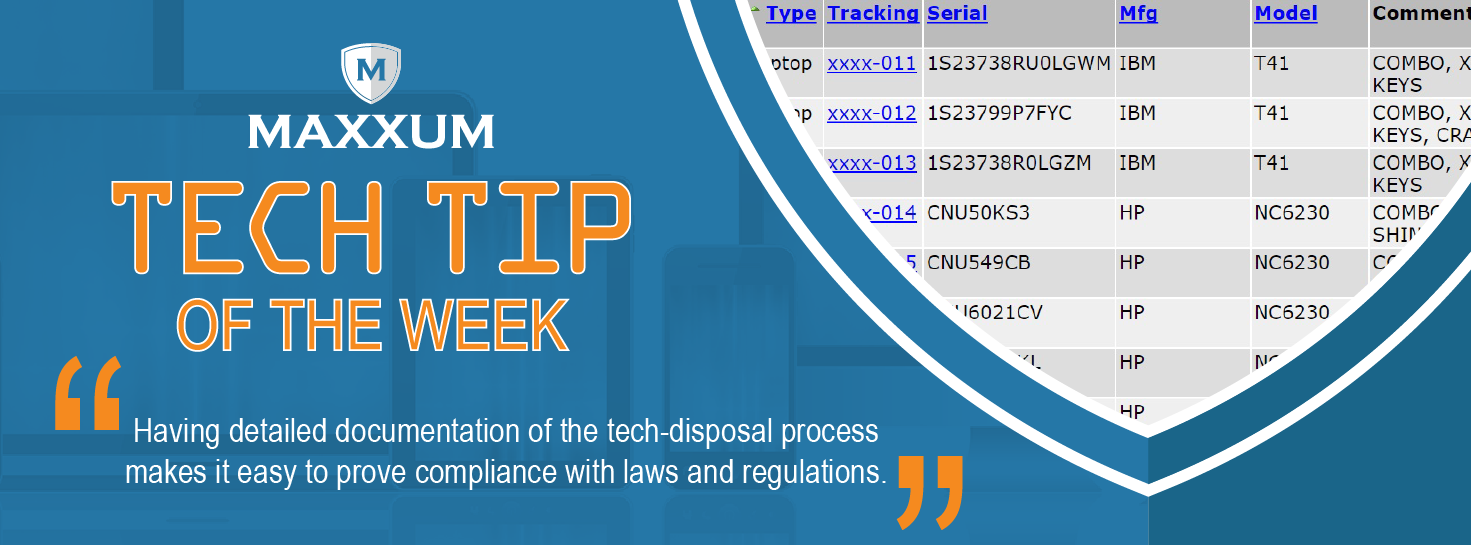
Maxxum has an easy process and makes it as simple as possible for school districts and institutions. Maxxum provides a full range of services to support any individual requirements. Our MaxxumSafe web portal makes asset tracking and record keeping transparent and simple. Maxxum also sells schools new and used equipment.
Throughout Maxxum’s history, and through our recent acquisition of Trace TM, we have worked with many clients in the education sector, providing data sanitization and remarketing services. Maxxum’s clientele has spanned the Twin Cities metro area, including public school systems in Edina, Fridley, Monticello and Owatonna, and Bethel College, Augsburg College, College of St. Scholastica and Capella University.
One of the advantages of working with Maxxum is that we are local. With two facilities in the Twin Cities, we’re able to get to know and meet with our school partners and prospects to understand their needs and requirements. Questions we ask our education partners include:
- How do they value their equipment?
- Why are they turning over their current equipment?
- What are the financial considerations?
- What is the greater purpose of remarketing the equipment?
- What are their expectations for disposition?
- What does the timing look like for their equipment refreshes?
- Have they explored secure and compliant data destruction?
The more information Maxxum has the more resourceful and better advisor we can be. Maxxum wishes all education institutions a great last few weeks of the current school year and congratulates you on another successful year. Maxxum encourages you to reach out to us if you have any questions at all about your IT equipment.